Proxy Re Encryption Key Generation
Proxy re-encryption allows a proxy to transform a ciphertext computed under Alice’s public key into one that can be opened by Bob’s secret key. There are many useful applications of this primitive. Usage of pairings in proxy re-encryption algorithm. Both the key and re-encryption key generation parts are easy to understand, they're the same as in a regular. In a proxy re-encryption scheme, a proxy can convert an encryption computed under Alice’s public-key into an encryption intended for Bob. Such a scheme can be used by Alice to temporarily forward encrypted messages to Bob without giving him her secret key.
A Proxy Re-Encryption library using Bilinear Map. It contains basic functions like encryption, decryption, re-encryption, re-decryption, sign and verify.
Usage
On inputting a secret key sk 1 and a public key pk 2, the re‐encryption key generation algorithm ReKeyGen outputs a unidirectional re‐encryption key. On inputting a re‐encryption key and a ciphertext C 1, the re‐encryption algorithm ReEnc outputs a re‐encrypted ciphertext C 2 or ⊥. Proxy re-encryption (PRE) is a cryptographic primitive in which a proxy can transform Alice’s cipher- texts into ones decryptable by Bob. Key-private PRE specifies an additional level of security, requiring that proxy keys leak no information on the identities of Alice and Bob. The function of proxy re-encryption with keyword search (PRES) is the combination of proxy re-encryption (PRE) and public key encryption with keyword search (PEKS). However, a PRES scheme cannot be obtained by directly combining those two schemes, since the resulting scheme is no longer proven secure in our security model.
Setup
Set the generators of G1 and G2. It must pefrom at first.
Generate Random Element in Fr
PRE is supposed to encrypt symmetric key.
It's recommended to get the key from a random element in Fr and convert it to hex string instead of generating a random key and mapping it to Fr.
Generate Key Pairs
Generate key pairs of Delegator(A) and Delegatee(B).
You can get public key from existing secret key using getPkFromG1 and getPkFromG1.
Encryption & Decryption
A can of course encrypt and decrypt.
Generate Re-Encryption Key
A can generate reKey with A's secret key and B's public key.
Re-Encryption & Re-Decryption
Anyone can convert encrypted with reKeyinto ciphertext that can be decrypted by B.
Proxy Re Encryption
Sign and Verify
Right now only signature by delegator is implemented, delegatee can have key pair with delegator's format (in G1) as well.
Tips

Almost every input parameters can either be hex string or Object in group. It'll automatically check the type and convert it to Object during caculation if necessary.
Algrithom
Encryption Key Example
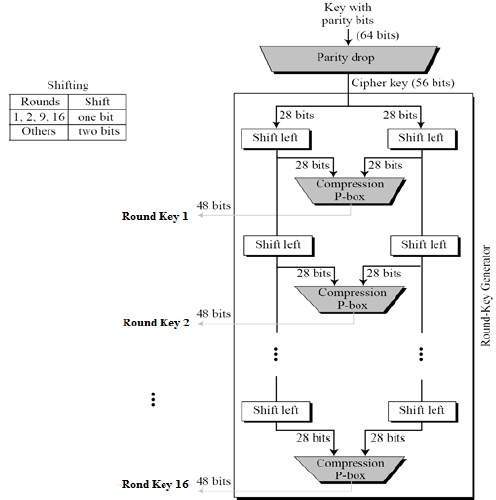
Encryption Key Example
Setup
$g$ and $h$ are the generators of $G_1$ and $G_2$
$Z=e(g,h)$
$e:G_1 times G_2 to G_T$
Spore galactic adventures serial key generator. Key Generation
$sk_A in F_r$, $pk_A=g^{sk_A} in G_1$
$sk_B in F_r$, $pk_B=h^{sk_B} in G_2$
Encryption$$C_1=((pk_A)^k,mZ^k)$$
Decryption
$$frac{beta}{e(alpha,h)^{frac{1}{sk_A}}}=frac{me(g,h)^k}{e((pk_A)^k,h)^{frac{1}{sk_A}}}=frac{me(g,h)^k}{e((g^{sk_A})^k,h)^{frac{1}{sk_A}}}=m$$
Re-Encryption Key Generation
$$rk_{A to B}=(pk_B)^{frac{1}{sk_A}}$$
Re-Encryption
From $C_I=(alpha,beta)$
Caculate $alpha{'}=e(alpha,rk_{P to D})$
Output $C_2=(alpha ^{'},beta)$
Re-Decryption
$$frac{beta}{(alpha^{'})^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e(alpha,rk_{P to D}))^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e((pk_A)^k,(pk_B)^{frac{1}{sk_A}})^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e((g^{sk_A})^k,(h^{sk_B})^{frac{1}{sk_A}})^{frac{1}{sk_B}}}=m$$
Sign
$$S=H^{sk_A}$$
VerifyGenerated key for norton antivirus 2019.
$$e(g,S)=e(g,H^{sk_A})=e(g^{sk_A},H)=e(pk_A,H)$$