Ansible Playbook Generate Ssh Key
- Ansible Playbook Generate Ssh Key Github
- Generate Ssh Key Aix
- Ansible Playbook Ssh User
- Generate Ssh Key Putty
I'm trying to re-generate ssh host keys on a handful of remote servers via ansible (and ssh-keygen), but the files don't seem to be showing up.The playbook runs OK, but the files on the remote are not altered. Apr 30, 2018 Server Fault asked. I’m trying to re-generate ssh host keys on a handful of remote servers via ansible (and ssh-keygen), but the files don’t seem to be showing up.The playbook runs OK, but the files on the remote are not altered. Whether this module should manage the directory of the authorized key file. If set, the module will create the directory, as well as set the owner and permissions of an existing directory. Be sure to set managedir=no if you are using an alternate directory for authorizedkeys, as set with path, since you could lock yourself out of SSH access.
Both comments really helped thanks. Turns out, my issue was caused by not passing the host and passing the wrong var name in my inventory, it should be ansiblesshprivatekeyfile –. Aug 14, 2015 Use Ansible to Add Users and their SSH public Keys on Multiple Linux Servers August 14, 2015 Andrew Galdes 3 This article demonstrates how to create an Ansible PlayBook that will add users to multiple Linux systems and add their public SSH key allowing them to login securely. Generate SSH Keys Ansible Role This Ansible role generates a unique public/private ssh keypair for each host (ssh client), and then copies the public key to an ssh server. This allows for quickly setting up ssh access to 1 server from many hosts in Ansible's inventory.
Purpose
This Ansible Playbook will assist on establishing passwordless SSH logins with the remote hosts you wish to manage. Windows 7 ultimate product key generator asus. Passwordless logins is a great convenience when connecting to multiple servers, via Ansible or not!
Download the tool
/triple-des-key-generator-c.html. Clone the repository to your ansible-enabled host:
Alternatively, you can download the ansible_setup_passwordless_ssh.yml and hosts from this repository.
Prerequisites
Make sure your Ansible host is equipped with the utilities, and that they are available to the PATH of the user you will be running the playbook as.
- ssh-keygen
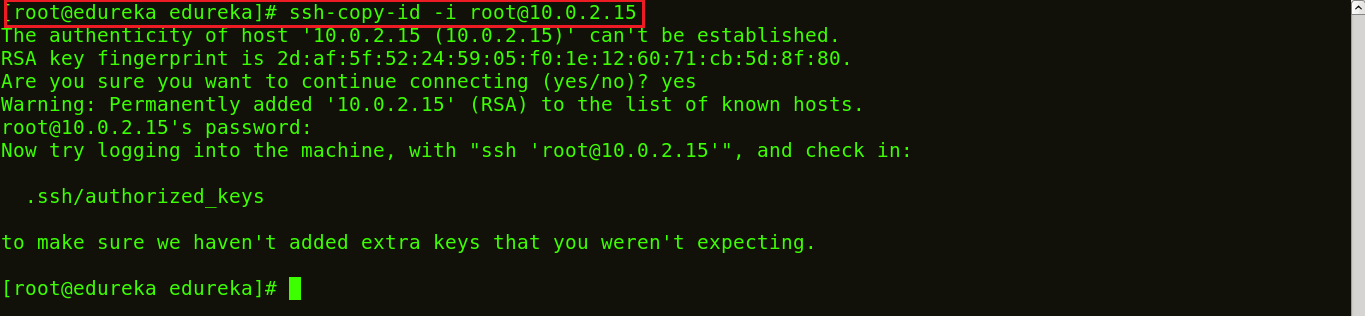
- ssh-copy-id
- sshpass
If you dont have them, before continuing you will have to install them using the recommended ways for your Linux distribution.
Preparations before you run
Edit the hosts file and define your environment's information. Fill in using the below matrix:
| Name | Description |
|---|---|
| local_host -> ansible_user | user of your localhost |
| local_host -> ansible_password | the password of your localhost's account |
| local_host -> ansible_port | if your local_host has the SSH daemon running not on the default port (22) |
| local_host -> ansible_host | if you want to define the IP of your local_host |
| ssh_key_filename | the filename of the new SSH key to be generated and stored under your .ssh folder of your localhost. |
| remote_machine_username | the username of the remote machines. If you are applying the procedure to multiple hosts. |
| remote_machine_password | the password of the 'remote_machine_username' remote machines. |
| [ansible_setup_passwordless_setup_group] | fill in the list of hosts that you want to establish the passwordless login with. the ansible_user is used only when executing the ansible_setup_passwordless_ssh_rollback playbook and it should match the remote_machine_username. The ansible_host can be ommitted if local_host can resolve the hostname you defined in first column. the ansible_port variable should be present even if it has the default value of 22, else you will have to modify the relevant task in the playbook. |
If you are planning to run the script towards multiple hosts, make sure the username/password you defined is the same to all of them!
Example
How to run it
run:
Last task in the playbook is to connect to each of those hosts and run some commands ('hostname' and 'id'), check the output to verify the success of the tool!
How to avoid the confirmation question.
by design, the 2 playbooks ask for the user's confirmation before proceeding to the tasks. This is a common safety practice, giving the user one last chance to think if he is ready to proceed with this execution.Nevertheless, if this is an unwanted behavior that you want to bypass, you can:
Ansible Playbook Generate Ssh Key Github
- skip this pre_task, by appending in the command the
-e confirmation=YESargument. For example:
- use the playbooks that are stored in the
non_interactivefolder. They are just missing this 'safety' check.
What happens in the background to your machines when you run the playbook
Generate Ssh Key Aix
By running this playbook, these things happen to your hosts:
Localhost:
- An SSH key is generated and placed under .ssh folder. Its file name is configurable, default is ansible_rsa.
- This SSH key is added to the ~/.ssh/config file for SSH client to utilize it when connecting to remote hosts.
Remote hosts:
Ansible Playbook Ssh User
- The generated SSH key is propagated to the list of remote hosts you configured in hosts inventory file, and added to their ~/.ssh/authorized_keys file. This is done using the
ssh-copy-idlinux utility that is meant for this job.sshpasslinux utility is used to assist running the script without the need to prompt for user password.
How to rollback
Generate Ssh Key Putty
run: